Which Answer Best Describes the Identification Component of Access Control
If access is not specifically granted it. Includes any component of your security infrastructure that has been outsourced to a third-party.
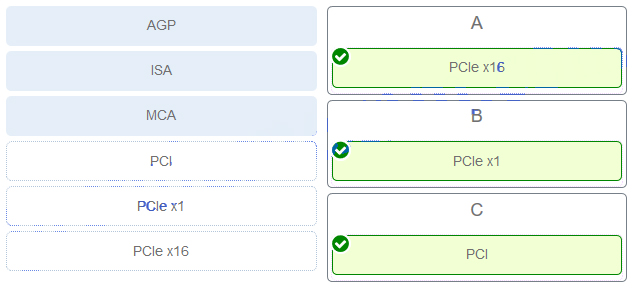
It Essentials V7 0 A 220 1001 Certification Practice Exam Answers
Identification is the method a subject uses to request access to a system.

. The preview shows page 5 - 6 out of 42 pages. Are intended to counter security attacks. There are multiple task types that may be available in this quiz.
It is considered prohibitive. Accountability is the process of creating and maintaining the policies and procedures necessary to ensure proper information is available when an organization is audited. The fundamental components in discretionary access controls are file and data ownership and access rights and permissions.
It should be used to integrate privacy policies and access control policies. The Clark and Wilson Integrity Model. Labels are associated with Mandatory Access Control MAC.
BIdentification is the method a subject uses to request access to a system. Then only as required by the job needs should access and privilege be granted. On a computer authorization typically takes the form of read write and execution permissions tied to a username.
Access control systems grants access to resources only to users whose identity has been proved and having the required permissions. Authorization is the third step of access control. MAC is not permissive.
These three elements of access control combine to provide the protection you. It is designed to test the skills and knowledge presented in the course. Most directories follow a hierarchical database format based on the X500 standard and a type of protocol as in Lightweight Directory Access Protocol LDAP that allows subjects and applications to interact with the directory.
Quizzes allow for partial credit scoring on. It is considered prohibitive. Administrative access control sets the access control.
One commonly-used example is identifying the risk profile of the user logging in. This problem has been solved. Authentication is the validation or proof that the subject requesting access is indeed the the same subject who as been granted that access.
A reduced level of control risk is. Protection against the unauthorized disclosure of data. Detailed access controls indicate the type of data that users can access based on the datas level of privacy sensitivity.
The point at which false acceptance and false rejection. Identification is the method a subject uses to request access to a system. To accomplish that we need to follow three steps.
Identification is the validation or proof that the subject requesting access is indeed the same subject who has been granted that access. It is an example of a discretionary access control model B. It is an extension of role-based access control D.
If the device being logged in from is not recognized that could elevate the risk to prompt additional authentication. Identification is the method a subject uses to request access to a system. A WAN is a LAN that is extended to provide secure remote network access.
Access control types include the following three that well look at one at a time. MAC is more secure and less flexible than DAC. Which answer best describes the identification component of access control.
This preview shows page 1 - 6 out of 42 pages. WAN is another name for the Internet. CIdentification is the process of determining who is approved for.
Component of access control. Which statement best describes access control. Authentication Identification authorization Q.
Types of Access Control. Connecting offices at different locations using the Internet can be economical for a business. Authentication is the validation or proof that the subject requesting access is indeed the.
AnswerRBAC Role Based Access Control Role-Based-Access-Control RBAC is a policy neutral access control mechanism defined around roles and privileges. Risk-Based Access Control is a dynamic access control model that determines access based on the level of evaluated risk involved in the transaction. You work as network administrator for an organization that has a Windows- based network.
You want to use multiple security countermeasures to protect the organizations information assets integrity. Some organizations start with allow all This should not be done because it presents a huge security risk. Which of the following is an example of a formal model of access control.
After obtaining an understanding of the internal control structure and assessing control risk of an entity an auditor decided not to perform tests of controls because. AIdentification is the validation or proof that the subject requesting access is indeed the same subject who has been granted that access. The components of RBAC such as role-permissions user-role and role-role relationships make it simple to do user assignments.
A WAN is a public utility that enables access to the Internet. Most enterprises have some type of directory that contains information pertaining to the companys network resources and users. Identification is the method a subject use to request access to a system.
Which answer best describes the accountability component of access control. Access control is paramount for security and fatal for. Which answer best describes the authentication component of access control.
The evidence obtained through tests of controls would not support an increased level of control risk. MAC is not permissive. Identification is the process of determining who is approved for access and what resources they are approved for.
The best access control policy is deny all This strategy starts by denying all access and privileges to all employees. Which answer best describes the authentication component of access control. Access control lists and role-based access control are types of discretionary access control.
Identification is the method a subject uses to request access to a system. The Equal Error Rate is equivalent to what. Identification is the method a subject uses to request access to a system.
How can a swipe card smart card or USB dongle be described. Prevention of unauthorized use of a resource. This quiz covers all of the content in Cybersecurity Essentials 11.

Identity And Access Management An Overview Sciencedirect Topics

Identity And Access Management An Overview Sciencedirect Topics
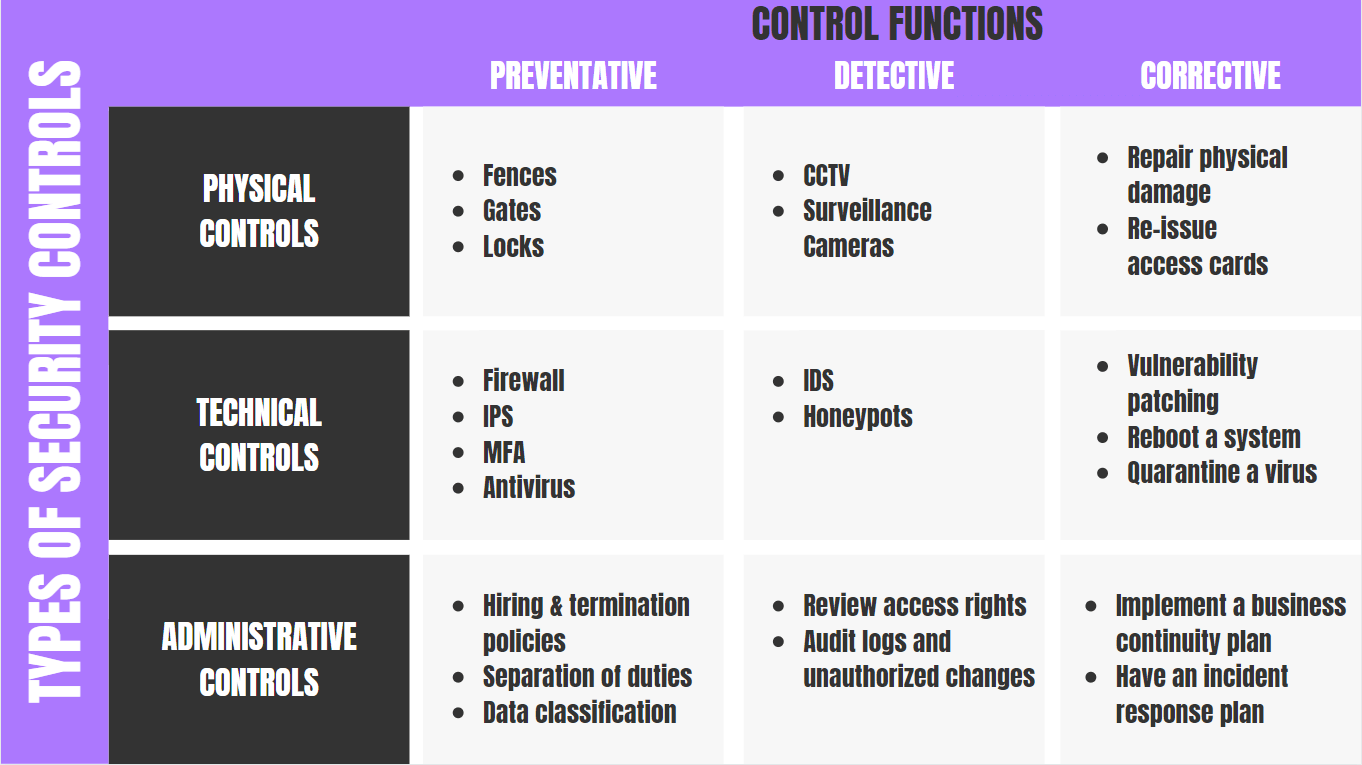
No comments for "Which Answer Best Describes the Identification Component of Access Control"
Post a Comment